Chapter 5 Digital Security Ethics and Privacy
Sign up for free. CHAPTER 5 DIGITAL SECURITY ETHICS AND.

An Ethical Approach To Data Privacy Protection
Play this game to review Computers.

. Visit this chapters premium content to complete the Checkpoint exercises complete the self. QUIZ Chapter 5 Digital Security Ethics and Privacy 78 average accuracy 60 plays University Computers a year ago by Jocel Lagnason Copy and Edit INSTRUCTOR-LED SESSION Start. A small text file that a web server stores on your computer Cracker Someone who accesses a computer or network illegally but has the intent of destroying data stealing infoor other.
The Consider This understanding of chapter concepts knowledge interactivel Discover More. Chapter 5 - digital security ethics and privacy By NigelTan1 Updated. Digital Security Ethics and Privacy Digital security risk- Event or action that could cause a loss of or damage to a computer or mobile device hardware software data.
Any event or action that could cause a loss of or damage to computer or mobile device hardware or software. The more common digital security risks include Internet and network attacks unauthorized access and use hardware theft software theft information theft and system failure. PowToon is a free.
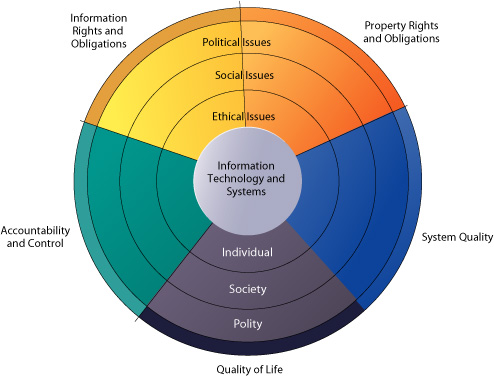
13 2019 254 pm. Checkpoint multiple choice Chapter 5252 Chapter 5 Digital Security Ethics And Privacy The page number ter concepts understandinn paeses after e. Ethics and Society Computer ethics are the moral guidelines that govern the use of computers and information systems Information accuracy is a concern Not all.
View EXERCISE 1_ CHAPTER 5 DIGITAL SECURITY ETHICS AND PRIVACYpdf from AIS 160 at Universiti Teknologi Mara.

Privacy Is Power Reclaiming Democracy In The Digital Age By Carissa Veliz

Online Safety Poster Internet Safety Activities Internet Safety For Kids Safety Posters

No comments for "Chapter 5 Digital Security Ethics and Privacy"
Post a Comment